One of the many cyberattacks that has escaped recent media attention is an incident involving the Baltimore City State’s Attorney’s Office in Maryland. Yesterday, data from the incident was leaked.
The group known as Kairos added stattorney[.]org to its leak site on March 31, 2025. At that time, Kairos claimed that they had acquired 325 GB of files and provided a number of screenshots as proof of their claims. The screenshots, which they partially redacted to mask sensitive information, suggested that they had acquired some really sensitive information on victims of crimes and perpetrators. One of the screenshots appeared to be the body of a man murdered as part of a gang war.
Despite sending multiple inquiries to the state office’s media contacts over a more than two-week period, DataBreaches received no reply to two simple questions: had the Baltimore City State’s Attorney’s Office confirmed that there had been a breach, and if so, what were they doing in response to it? As of publication today, there is still nothing on their website to indicate that there has been any breach or cybersecurity incident.
But according to Kairos, the state attorney’s office did — and does — know about the breach. In encrypted communications with DataBreaches, Kairos stated that their general method is to give their targets 7 days to get in touch. “If the target doesn’t get in touch, we publish it on the website with a countdown.” In this case, they said, about 5 days after they listed the state agency on the leak site, “they wrote to us saying they hadn’t seen our messages and also said they were interested in us not posting anything. After that, we started negotiations.”
The negotiations were reportedly short-lived and unsuccessful. “Office of the State’s Attorney for Baltimore City asked us for a listing of all the files we downloaded and also asked us to send 5 files of their choice. After that, negotiations ended., ” Kairos’s spokesperson told DataBreaches. But the state had reason to know even before that proof demonstration, as Kairos tells DataBreaches that their presence was detected while they were in the state’s system exfiltrating data.
Personal and Sensitive Data Leaked on Juvenile Offenders
According to Kairos, they did not encrypt or delete any files but just exfiltrated data.
DataBreaches’ inspection of the data tranche confirmed Kairos’s claims that they had downloaded a lot of criminal case files, including personal information about offenders and victims. Because many of the case files in the tranche are court cases with public records, DataBreaches will not describe them here. But many records in the tranche involved juveniles and provided demographic data as well as details of their crimes, their placement, treatment, and vocational retraining etc. Juveniles’ records may often be sealed or subsequently expunged. DataBreaches does not know the status of all of the juveniles’ cases, but this leak put detailed, multi-page reports about juveniles into the public domain, which may affect them for the rest of their lives if they seek jobs or educational opportunities.
In addition to the individual multi-page reports on juvenile offenders, DataBreaches also noted some spreadsheets with data on juvenile offenders. One spreadsheet recorded 46 juveniles who were under 13 years old as of June 1, 2022. It listed their names, date of birth, race, gender, date of incident, type of incident, officer involved, outcome, notes, and other fields:

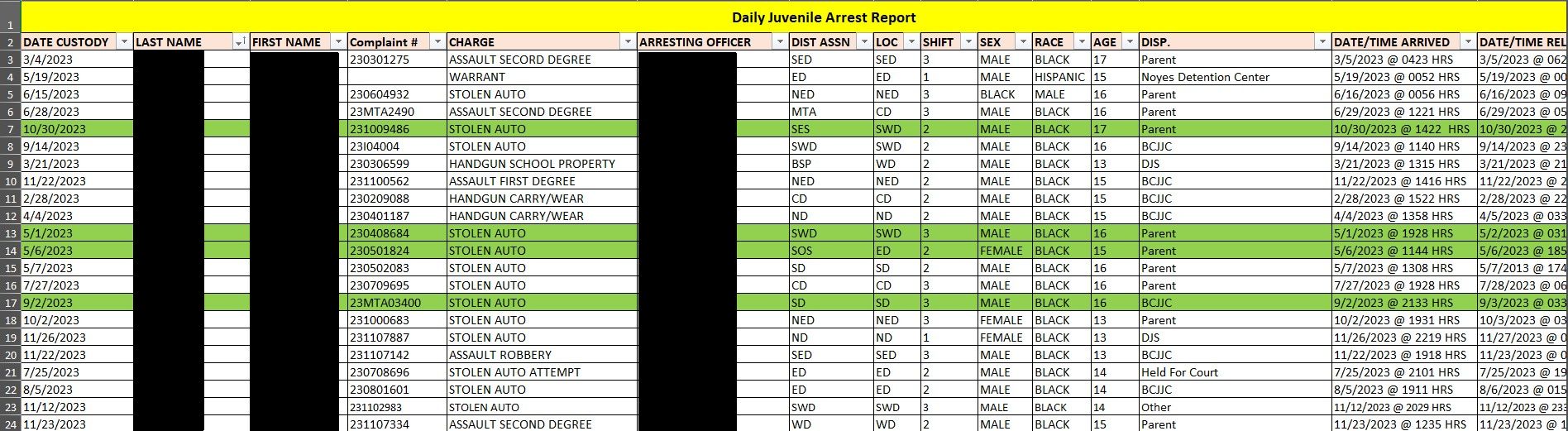
Another spreadsheet in the tranche recorded 586 juveniles who were arrested in 2023. This particular spreadsheet did not list their date of birth, but did list their first and last name, the criminal charge, their race, gender, and age, and the disposition of the arrest.
Disciplinary and Personal Data on Police Department Personnel
But juveniles weren’t the only ones who had their personal information leaked. Although DataBreaches did not spot any databases with personnel data such as human resource data or payroll data, DataBreaches did spot reports on police officer investigations from the Internal Affairs Department and the Baltimore Police Department Bureau of Public Integrity. DataBreaches also spotted a spreadsheet created in 2022 with names, ranks and what appeared to be personal phone numbers of more than 6,350 members of the Baltimore Police Department. From a Google search, some of those individuals are no longer with the department but appear to still have the same phone numbers. Others in the list appear to still be active employees of the police. No attempt was made to determine how many were currently employed and still associated with those phone numbers.
Victim and Witness Data
While much of the personal and non-public data that DataBreaches noted involved perpetrators and defendants, some of the files concerned witnesses and victims of crimes. Those also contained personal and in some cases, sensitive, information.
As noted earlier, Baltimore City State’s Attorney’s Office did not respond to multiple email inquiries about this breach and there is nothing on their site about any breach. DataBreaches will continue to monitor their site for any disclosure or information about their incident response.